Installing THC Hydra
Download THC hydra from https://github.com/vanhauser-thc/thc-hydra.
Once downloaded, extract the files, and execute the following:
./configure
make
make install
If you’re using Ubuntu/Debian, type the following as well:
libgtk2.0-dev libmysqlclient-dev libpq-dev libsvn-dev \
firebird-dev libmemcached-dev libgpg-error-dev \
libgcrypt11-dev libgcrypt20-dev
CLI Usage
Here, we examine how to use hydra with common protocols.
SSH/FTP/RDP/TELNET/MYSQL
One must remember that Hydra can deal with approximately 55 different protocols. These are but a few examples of the most dealt-with protocols, such as ssh, ftp, rdp, telnet, and mysql. However, the same principle applies to the remaining protocols.
In order to get Hydra to work with a protocol, you’ll need either a username (-l) or a list of usernames (-L), a list of passwords (a password file), and the target IP address associated with the protocol. You can add further parameters if you wish. For example, -V for verbosity.
Alternatively, you can also format it as follows:
-l or -L: username or list of usernames to attempt
-P: password list
-s: port
-V: verbose
<protocol>: ftp/rdp/ssh/telnet/mysql/etc…
<ip>: ip address
For example, for FTP:
Or
HTTP-GET-FORM
Depending on the type of request, GET or POST, you can use either http-get-form or http-post-form. Under the inspect element, you can figure out whether the page is a GET or POST. You can then use the http-get-form when attempting to find the password to a username:password combination on the web (for instance, a website).
-l or -L: username or list of usernames to attempt
-P: password list
-f : stop when the password is found
-V: verbose
a: login page
b: username/password combination
c: error message received if login fails
d: H=session cookie
For example, suppose we wish to hack DVWA (Damn Vulnerable Web Application). Once online using apache2, it should be at your local IP. In my case, it’s at http://10.0.2.15.
So, the:
<ip>: 10.0.2.15
a: /vulnerabilities/brute/
Next, we need b and c. So, let’s try to login with fake credentials (anything here will do). The site displays this message: “Username or password incorrect.” Therefore, we will use the message c:
c: username or password incorrect
So, b will be as follows:
Replace the credentials inputted with ^USER^ and ^PASS^. If this was a POST request, you would find this information under the inspect element > Request tab.
Next, under inspect element, copy the cookie. This will be d:
So, for example:
When you run this, and if the password is in the list, then it will find it for you.
However, if this proves to be too much work for you, no need to stress out because there’s a GUI version as well. It is a lot simpler than the CLI version. The GUI version of THC hydra is called Hydra GTK.
Installing Hydra GTK
In Ubuntu, you can simply install Hydra GTK using the following command:
Once installed, you will need the following:
- A target or list of targets: This is the IP address of the protocol you wish to attack
- Port number: the port number associated with the protocol
- Protocol: ssh, ftp, mysql, etc…
- Username: either input a username or a list of usernames
- Password or Password list
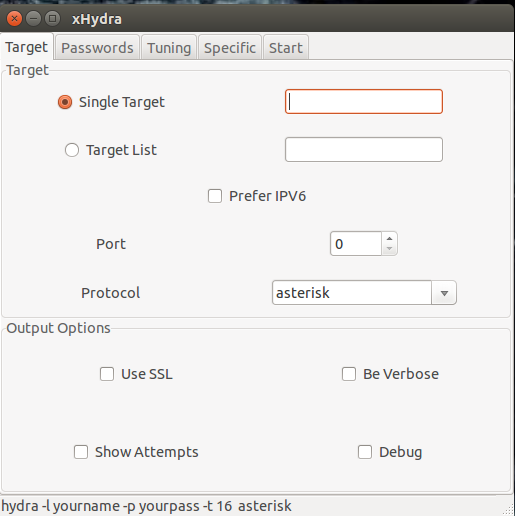
Depending on whether you want to hack one or multiple targets, you can either input one or many targets into the target box. Suppose you’re attacking a single target, an SSH, located at 999.999.999.999 (a fake IP address, obviously). In the target box, you’d put 999.999.999.999, and in the port section, you’d put 22. Under the protocol, you’d put SSH. It would be advisable to tick the “be verbose” and the “show attempts” boxes as well. The “be verbose” box is equivalent to -v in THC Hydra, while the “show attempts” box is equivalent to -V in THC Hydra. The plus point about Hydra is that it can deal with a large number of protocols.
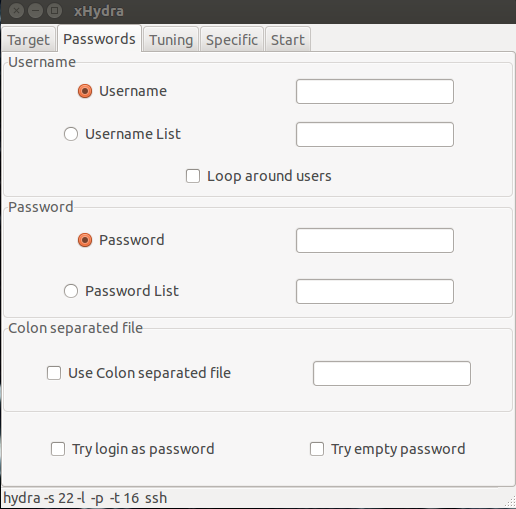
In the next tab, input the username you desire or a list of usernames (the location of the list of usernames in this case). For instance, in the “username list”, I would put “/home/kalyani/usernamelist.txt”. The same is true for passwords. The location of the password file is inputted in the box called “password list”. Once these have been filled in, the rest is easy. You can leave the tuning and specific tabs as is and click on the start button under the start tab.
Hydra GTK is a lot easier to use than THC Hydra, even though they are the same thing. Whether you use THC Hydra or Hydra GTK, both are great tools to crack passwords. The problem typically encountered will come in the form of the password list used. You can obviously use other programs such as crunch and wordlist generators to tailor your password list to your liking. However, if you can also tailor the password list to your use, Hydra can become a very powerful ally.
Happy Hacking!