Nmap
Network Mapper, commonly used as Nmap, is a free and open-source tool for Network and Port scanning. It is also proficient in many other active information gathering techniques. Nmap is by far the most widely used information-gathering tool used by penetration-testers. It is a CLI based tool, but it also has a GUI based version in the market named Zenmap. It was once a “Unix Only” tool but now supports many other operating systems such as Windows, FreeBSD, OpenBSD, Sun Solaris, and many others. Nmap comes pre-installed in penetration testing distros like Kali Linux and Parrot OS. It can also be installed on other Operating Systems. To do so, seek Nmap here.
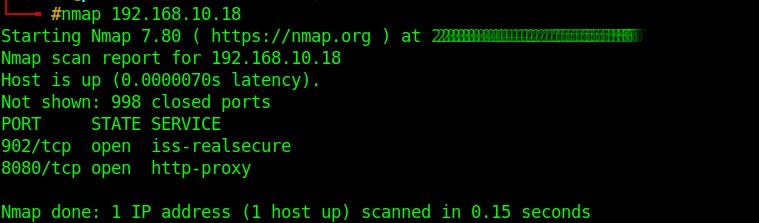
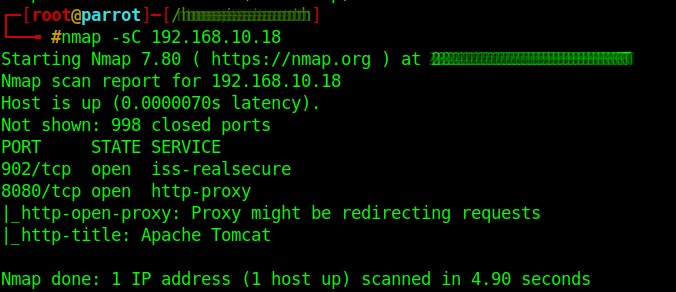
Figure 1.1 shows you a normal scan and results. The scan revealed the open ports 902 and 8080. Figure 1.2 shows you a simple service scan, which tells what service is running on the port. Figure 1.3 shows a default script scan. These scripts sometimes reveal interesting information that can be further used in the lateral parts of a pen-test. For more options, type nmap in the terminal, and it will show you the version, usage, and all other options available.
Fig 1.1: Simple Nmap scan
Fig 1.2: Nmap service/version scan
Fig 1.3: Default script scan
Tcpdump
Tcpdump is a free data-network packet analyzer that works on the CLI interface. It allows users to see, read, or capture network traffic being transmitted over a network that is attached to the computer. Originally written in 1988 by four workers at Lawrence Berkely Laboratory Network Research Group, it was organized in 1999 by Michael Richardson and Bill Fenner, who created www.tcpdump.org. It works on all Unix-like operating systems (Linux, Solaris, All BSDs, macOS, SunSolaris, etc). The windows version of Tcpdump is called WinDump and uses WinPcap, the windows alternative for libpcap.
To install tcpdump:
Usage:
For options detail :
Wireshark
Wireshark is an immensely interactive network traffic analyzer. One can dump and analyze packets as they are received. Originally developed by Gerald Combs in 1998 as Ethereal, it was renamed Wireshark in 2006 due to trademark issues. Wireshark also offers different filters so the user can specify what type of traffic to be shown or dumped for later analysis. Wireshark can be downloaded from www.wireshark.org/#download. It is available on most of the common Operating Systems (Windows, Linux, macOS), and comes pre-installed in most penetration distros like Kali Linux and Parrot OS.
Wireshark is a powerful tool and needs a good understanding of basic networking. It converts the traffic into a format that humans can easily read. It can help the users troubleshoot latency problems, dropped packets, or even hacking attempts against your organization. Moreover, it supports up to two thousand network protocols. One may not be able to use all of them as common traffic consists of UDP, TCP, DNS, and ICMP packets.
Amap
Application Mapper (also amap), as the name may suggest, is a tool to map applications on open ports on a device. It is a next generation tool that can discover applications and processes even when they are not running on their conventional ports. For example, if a web server is running on port 1337 instead of the standard port 80, amap can discover this. Amap comes with two prominent modules. First, amapcrap can send mock data to ports to generate some kind of response from the target port, which can later be used for further analysis. Second, amap has the core module, which is the Application Mapper (amap).
Amap usage:
amap v5.4 (c) 2011 by van Hauser <vh@thc.org> www.thc.org/thc-amap
Syntax: amap [Modes [-A|-B|-P]] [Options] [TARGET PORT [port]...]
Modes:
-A (Default) Send triggers and analyze responses (Map Applications)
-B Grab banners ONLY; don’t send triggers
-P A full-fledged connect port scanner
Options:
-1 Speedy! Send triggers to a port until 1st identification
-6 Use IPv6 instead of IPv4
-b Print ASCII banner of responses
-i FILE Machine-readable output file to read ports from
-u Specify UDP ports on the command line (default: TCP)
-R Do NOT identify RPC service
-H Do NOT send potentially harmful application triggers
-U Do NOT dump unrecognized responses
-d Dump all responses
-v Verbose mode; use twice or more for more verbosity
-q Don’t report closed ports and do not print them as unidentified
-o FILE [-m] Write output to file FILE; -m creates machine-readable output
-c CONS Make parallel connections (default 32, max 256)
-C RETRIES Number of reconnects on connecting timeouts (default 3)
-T SEC Connect timeout on connection attempts in seconds (default 5)
-t SEC Response wait for a timeout in seconds (default 5)
-p PROTO Send triggers to this protocol ONLY (e.g. FTP)
TARGET PORT The target address and port(s) to scan (additional to -i)
Fig 4.1 Sample amap scan
p0f
p0f is the short form for “passive OS fingerprinting” (A zero is used instead of an O). It is a passive scanner that can identify systems remotely. p0f uses fingerprint techniques to analyze TCP/IP packets and in order to determine different configurations including the operating system of the host. It has the ability to perform this process passively without generating any suspicious traffic. p0f can also read pcap files.
Usage:
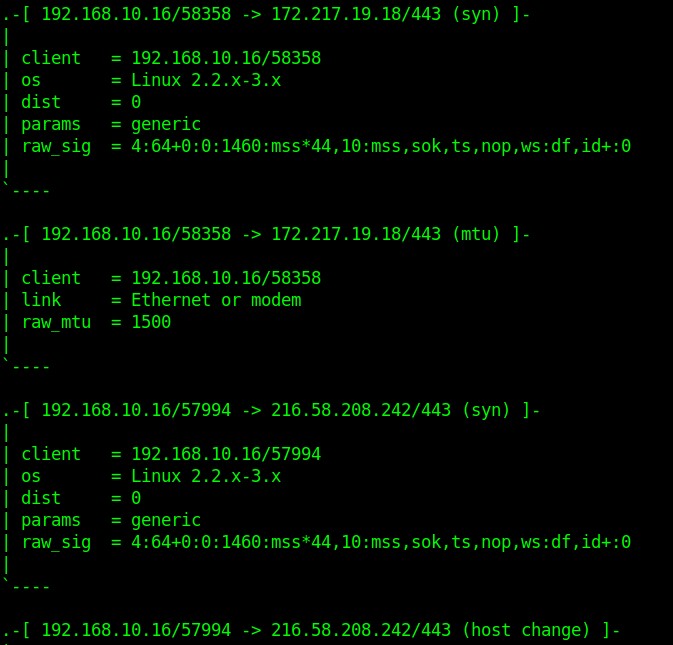
Fig 5.1 Sample p0f output
The host has to either connect to your network (spontaneously or induced) or be connected to some entity on your network by some standard means (web browsing, etc.) The host can accept or refuse the connection. This method is able to see through packet firewalls and is not bound by the restrictions of an active fingerprinting. Passive OS fingerprinting is mainly used for attacker profiling, visitor profiling, customer/user profiling, penetration testing, etc.
Cessation
Reconnaissance or Information Gathering is the first step in any penetration test. It is an essential part of the process. Starting a penetration test without a decent recon is like going to a war without knowing where and who you are fighting. As always, there is a world of amazing recon tools apart from the ones above. All thanks to an amazing open-source and cybersecurity community!
Happy Recon! 🙂